 Stambia
The solution to all your data integrations needs
Stambia
The solution to all your data integrations needs

Stambia Privacy Protect
Discover how Stambia's Privacy Protect module protects your personal data and meets regulatory requirements (GDPR, CNIL3), due to its features:
- for anonymization and pseudonymization of data
- for filling in databases from generated data
- for traceability and audit
"Privacy by design" natively integrated into your integration solution
Use cases of the Privacy Protect component
Replicating a data model with anonymization and/or pseudonymization
The case of anonymization
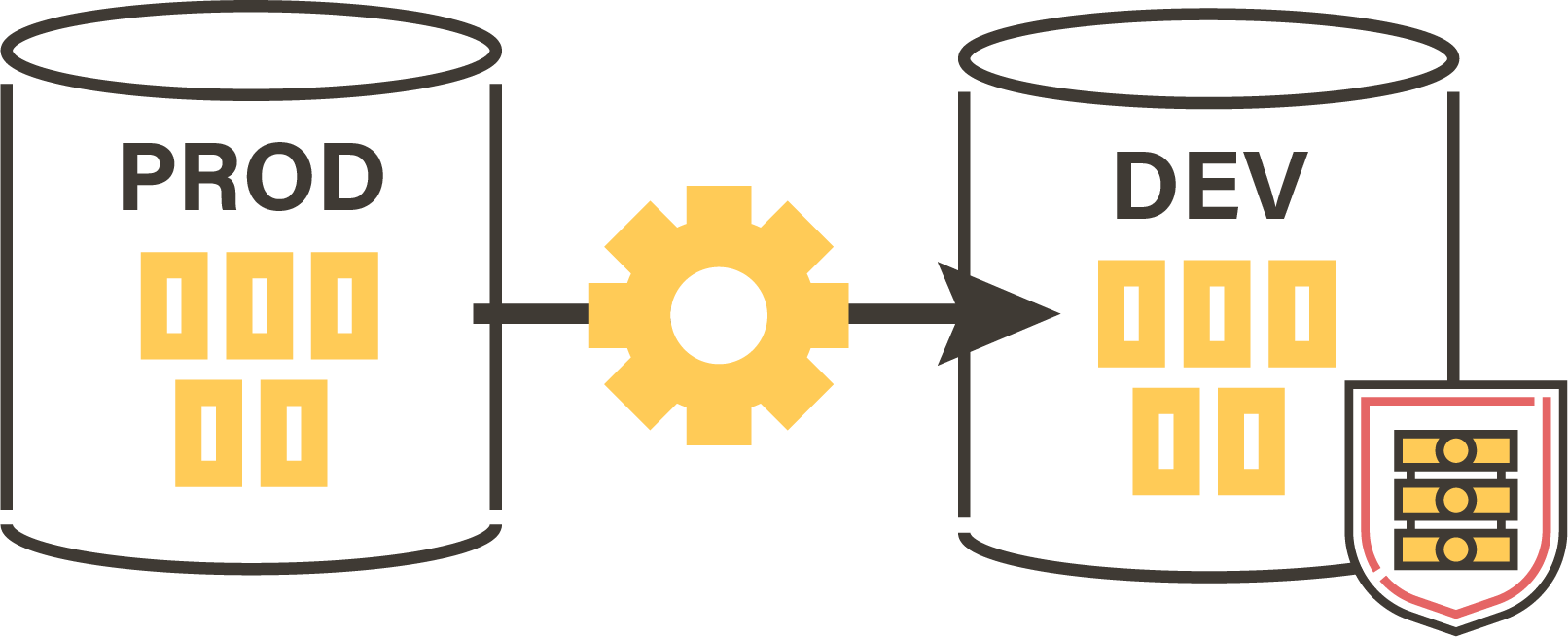
Data protection can consist in anonymizing development or test databases, by loading them from the real data of the production databases. Stambia Privacy Protect allows you to define the rules on metadata (tables, columns, etc.) and then perform the specified anonymization.
The case of pseudonymization
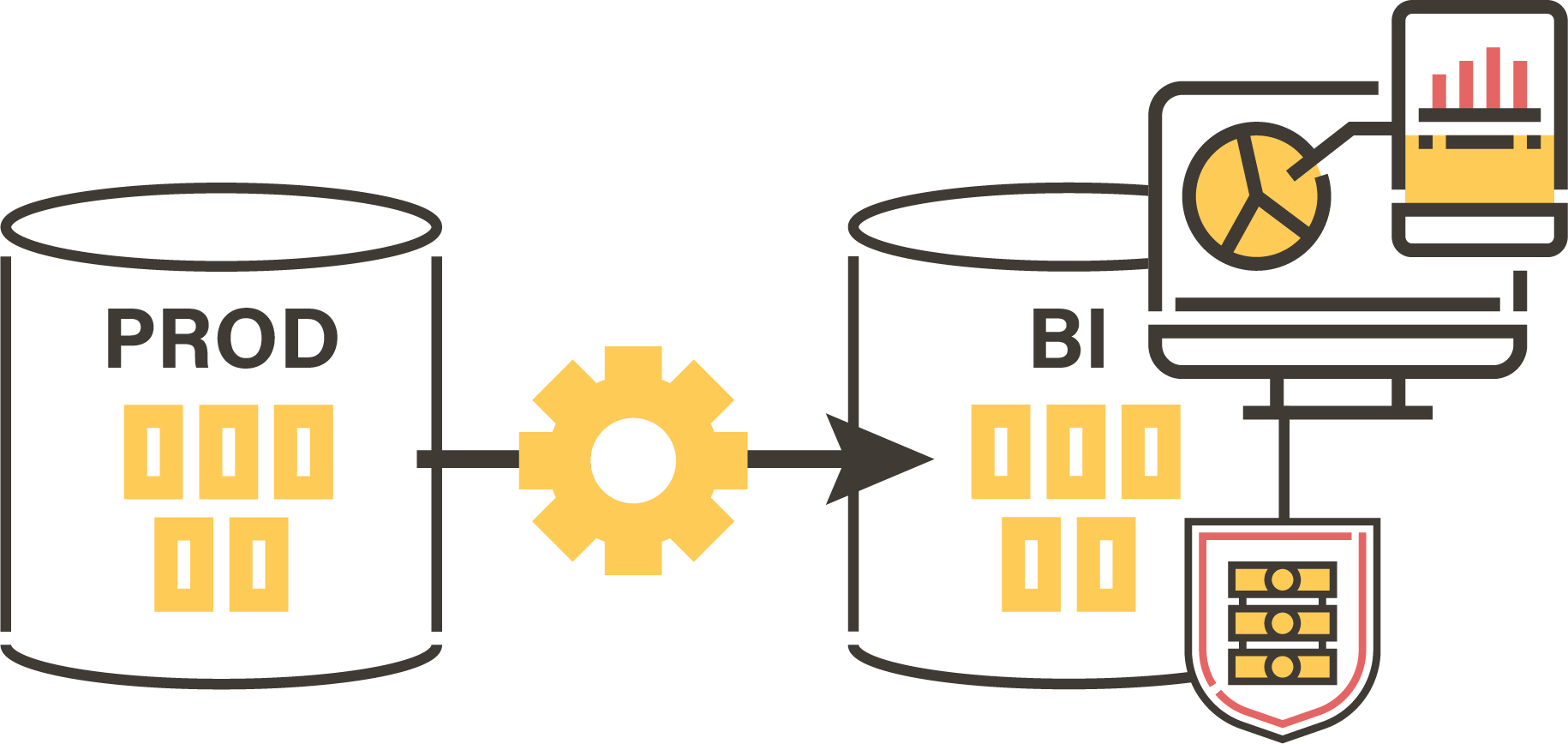
Pseudonymization may also be necessary to protect your data for analysis purposes:
- Expose data to the outside (Open data)
- Set up Analytics systems (Business Intelligence, Big Data, Machine learning)
Feeding a new database with randomly generated datasets
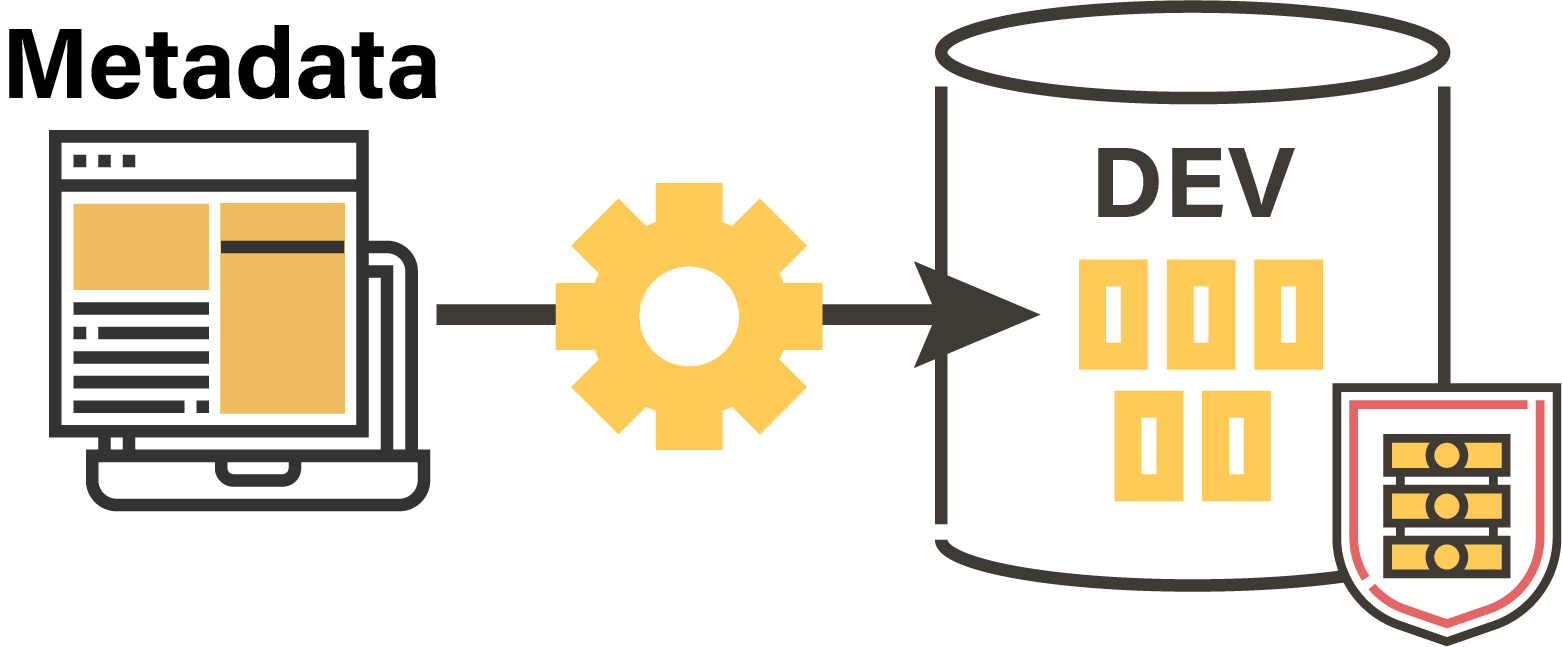
The development of new business applications or simply new business intelligence data models will require the creation of data sets during the development and testing phases. Stambia Privacy Protect automatically feeds new databases.
Certify the methods of protecting your personal data and compliance with the GPDR
The obligation of proof is one of the constraints of the GPDR. Every organization must show that it has taken the subject of privacy as part of its daily life. Stambia Privacy Protect makes it easy to set up audits and certifications, especially by automatic reports generated during any use of the component.
How does the component work ?
A component integrated into Metadata
The Privacy Protect component is fully integrated into the data integration solution, through Stambia's "Metadata". For each schema, table, column, the user can define his rules regarding anonymization, pseudonymization or data generation. These rules are then applied when the component is executed with the configured metadata.
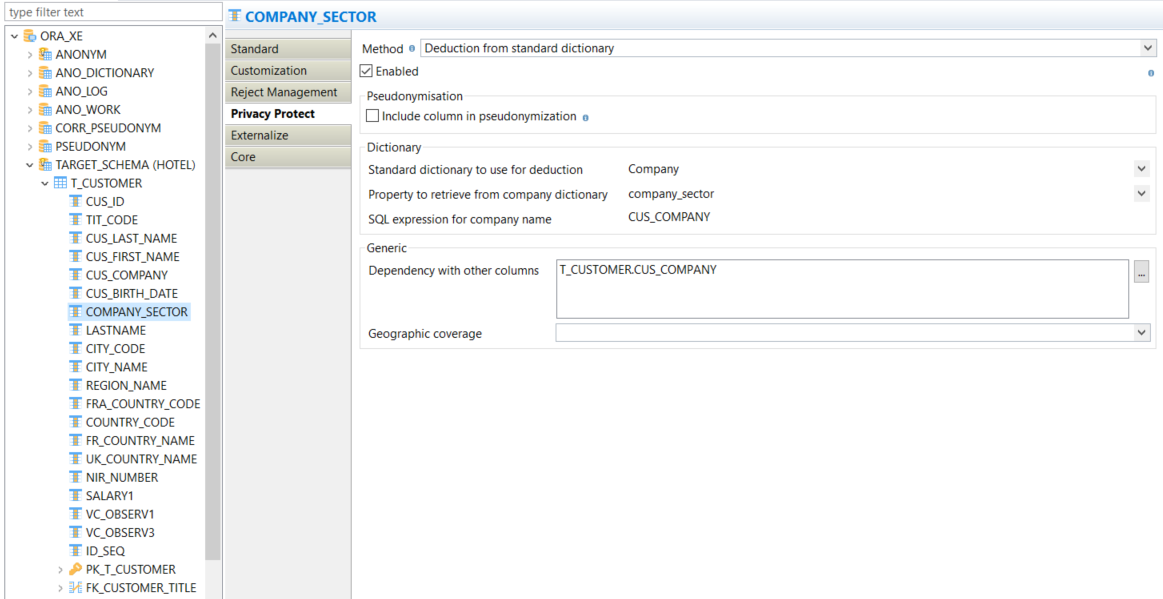
A complete range of functionalities
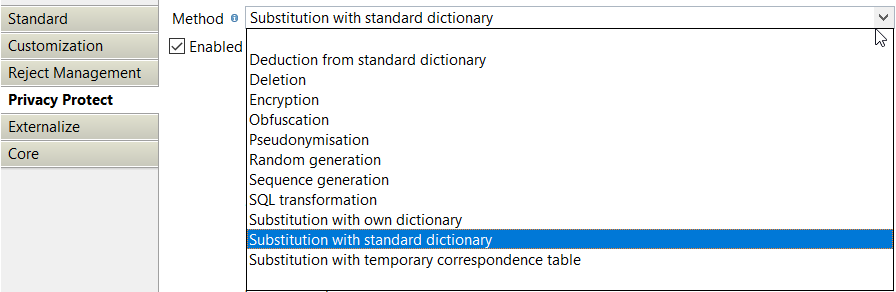
Several protection methods
- Substitution by provided or customized dictionaries
- Deduction from these dictionaries
- Generation of random values, automatic numbering
- Obfuscation, encryption, SQL transformation
- Generation of temporary correspondence tables, pseudonymization tables
Advanced features for these methods
- Several data distribution methods: taking into account (or not) the uniform distribution of data (uniform, by weight in the dictionary or by normal law)
- Intelligent processing of zero values
- Use of personalized masks (emails, phones,...)
- Taking into account the geographical particularities of your data
- Building HTML reports (anonymization/pseudonymization log, samples)
- Use of database engines (like Oracle, PostgreSQL)
- Loading empty tables from Privacy Protect methods
Technical specification and prerequisites
| Specification | Description |
|---|---|
|
Audit / traceability |
Reports in HTML format as well as in database |
| Supported encryption methods |
|
| Databases |
|
| Stambia Designer Version | Stambia Designer s19.1 |
| Stambia Runtime Version | Stambia Runtime S17.5.6 |
| Notes complémentaires |
|
Want to know more ?
Consult our resources
Did not find what you want on this page?
Check out our other resources:
Semarchy has acquired Stambia
Stambia becomes Semarchy xDI Data Integration


